The rise of the hybrid work model, where employees split their time between the office and remote locations, has become the new normal.
The following is a recent breakdown of the world’s working population:
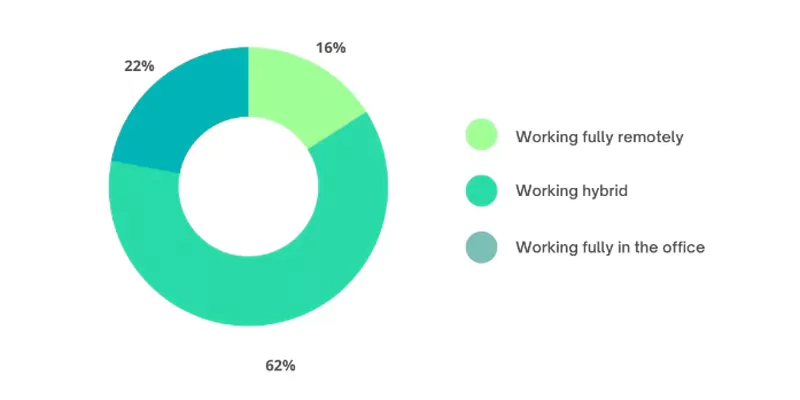
[Source]
In fact, owing to better work-life balance hybrid work provides, there is a positive trend in its favor compared even to a few years back
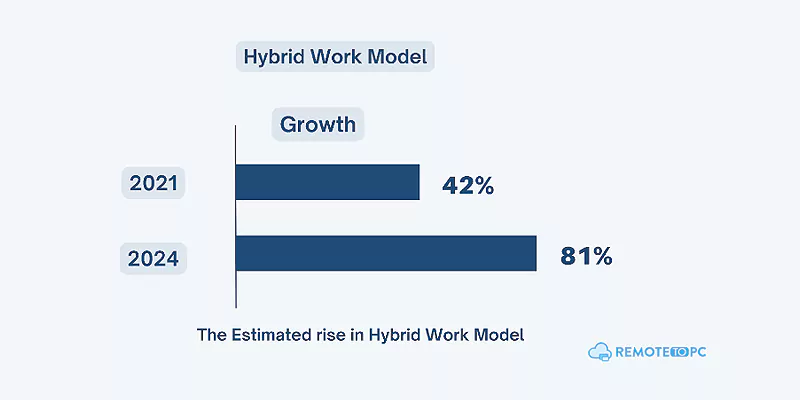
[Source]
While this flexibility offers numerous benefits, it also introduces new security challenges.
Securing remote access is crucial, and traditional security limitations in hybrid work often fall short in accommodating the latest trends.
The Rise of the Hybrid Work Model and the Importance of Secure Remote Access
The past few years have witnessed a dramatic shift towards hybrid work models. According to a study, this allows employees the flexibility to work from anywhere, fostering a better work-life balance and improved productivity.
However, this flexibility comes with the responsibility of ensuring secure remote access to company resources. Remote employees often connect from various devices and networks, making them more vulnerable to cyberattacks.
Challenges of Traditional Security Measures
Traditional security limitations in hybrid work like firewalls and VPNs have served well in securing on-premise networks. However, they struggle to adapt to the dynamic nature of a hybrid environment. Here’s why:
Limited Visibility
Traditional methods lack the ability to monitor and track activity beyond the initial access point (e.g., VPN). This creates blind spots, making it difficult to detect suspicious activity within the network.
Static Security Posture
Firewalls rely on predefined rules that may not be effective against evolving cyber threats.
Complexity and Scalability
Managing and maintaining traditional security measures can become complex and resource-intensive, especially in a rapidly scaling hybrid environment.
Benefits of IP Address Monitoring for Security
IP address monitoring tools address these limitations by continuously tracking and analyzing IP addresses associated with user activity. This provides several security benefits:
Enhanced Visibility
IP monitoring provides a comprehensive view of all devices accessing the network, regardless of location. This allows security teams to identify unauthorized access attempts, unusual activity patterns, potential breaches, along with networking and troubleshooting.
Dynamic Security
Network IP monitoring tools can be configured to set dynamic access controls based on real-time risk assessments. This allows for a more granular and adaptable security posture.
Improved Threat Detection
By analyzing IP geolocation and historical data, IP monitoring tools can help identify suspicious login attempts originating from unusual locations or devices. This enables faster detection and mitigation of potential threats.
Hybrid Work Security Best Practices
While IP address monitoring tools are a powerful tool, they should be implemented alongside a comprehensive set of hybrid work security best practices.
Here are some key recommendations:
Educate Employees
Foster a culture of cybersecurity awareness by regularly training employees on common threats, phishing scams, and secure password practices.
Enforce Strong Password Policies
Implement strong password policies that require complex passwords and regular changes. Consider multi-factor authentication (MFA) for added security.
Secure Company Devices
Implement endpoint security solutions and ensure all company devices are up-to-date with the latest security patches.
Segment the Network
Divide the network into different segments to limit access to sensitive data and resources, only granting access based on the principle of least privilege.
Monitor Network Activity
Regularly monitor network activity for suspicious behavior and leverage real-time monitoring capabilities to identify and address threats promptly.
Control Remote Access
Implement secure access controls for remote connections, such as requiring VPN access and restricting access to specific resources.
Embracing the Change With Awakish IP Address Monitoring Tools
Awakish offers free IP address monitoring tools designed specifically for the needs of hybrid work environments. These tools provide comprehensive real time monitoring, empowering organizations to:
Secure remote access
Ensure only authorized devices and users can access company resources, regardless of location.
Simplify security management
Automate tasks and gain real-time insights into network activity, reducing the burden on security teams. This can be particularly helpful for IT infrastructure management.
Proactively address threats
Identify and mitigate potential breaches before they cause significant damage.
Ace your hybrid work’s security with Awakish’s free website performance monitoring tools. Sign up now!



